Let’s begin 2025 with an understatement about last year: 2024 was an eventful year for cybersecurity. That in itself is no surprise. The specifics, though, looked like this: AI use accelerated (for good and for bad), ransomware surged and relentless attacks on third parties shifted focus to cyber resilience.
Since history tends to repeat itself if we don’t learn from it, let’s revisit some of the most notable cyber themes and events of 2024 to help you navigate the cyber unknowns of 2025.
AI’s “iPhone moment.” The rapid evolution and mass adoption of GenAI tools ushered in AI’s “iPhone moment” in 2024. Individuals embraced AI to improve countless daily activities while enterprises invested heavily to disrupt customer-facing applications, back-end infrastructure, workforce empowerment and everything in between. An October 2024 PwC survey found that 49% of technology leaders said AI was “fully integrated” into their companies’ core business strategy. A third of respondents said their companies had fully integrated AI into products and services. And the unprecedented pace of AI innovation and investment continues.
AI is transforming cybersecurity, like so many other facets of business. CyberArk research shows that nearly all organizations (99%) used GenAI in their identity-related cybersecurity initiatives in 2024. Unfortunately, the bad guys used it too. In the last 12 months, nine of 10 organizations were victims of a breach due to a phishing or vishing attack. These attacks will only get more challenging to detect as cybercriminals increasingly use AI to create hyper-personalized phishing emails, automate large-scale attacks and uncover vulnerabilities faster than ever.
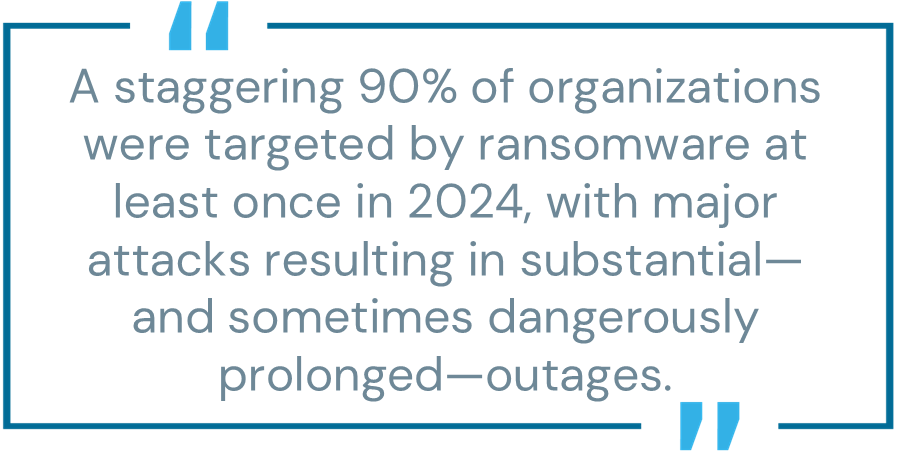
Relentless ransomware. Ransomware attacks continued to increase in frequency, scale and severity of impact throughout 2024. A staggering 90% of organizations were targeted by ransomware at least once. Major attacks on healthcare, finance and critical infrastructure organizations resulted in substantial—and sometimes dangerously prolonged—outages. For instance, a ransomware attack on the Port of Seattle disrupted the Seattle-Tacoma International Airport for weeks in the fall. An attack on a top U.S. healthcare group subsidiary shut down operations at hospitals and pharmacies for over a week, resulting in $872 million in “unfavorable cyberattack effects.” Other victim organizations paid tens of millions of dollars in ransom payments. Unfortunately, of those organizations affected by ransomware, 75% paid the ransom but did not recover their data.
Despite law enforcement crackdowns around the world, 2024 saw a 30% year-over-year increase in the number of active ransomware groups. This is further proof that ransomware is here to stay and, in fact, will continue to increase in volume and sophistication with AI-enabled deepfakes.
Weaponized deepfakes. This brings us to our next central theme. Threat actors increasingly embraced deepfake tactics in 2024, thanks to cheap, widely accessible GenAI tools that can manipulate audio, video and image content. In a pivotal election year—during which more than four billion people voted for leaders—deepfake technology was weaponized to sow confusion and mistrust. Though many election-related deepfakes that circulated were relatively easy to disprove, they polluted the election information ecosystem and hinted at greater challenges ahead.
As AI continues to advance, digital disinformation is also infiltrating the enterprise, posing risks in the form of financial loss, reputational damage and corporate espionage that will continue to grow in the year ahead.
Multi-phase Microsoft email breach. In early 2024, Microsoft disclosed that a Russian state-sponsored group known as Midnight Blizzard (aka APT29) had breached their corporate email servers via a password spray attack and had stolen sensitive data from staff emails.
The attackers hit the company again in March using information from stolen emails. Later, CISA confirmed that emails between U.S. federal agencies and Microsoft were stolen in the attack. These emails contained information that let the threat actors gain access to some customers’ systems. In response, the U.S. federal cyber agency issued an emergency directive saying the breach “presents a grave and unacceptable risk to agencies,” and a congressional hearing followed.
Volt Typhoon activity. A Chinese state-sponsored cyber gang known as Volt Typhoon compromised the IT environments of multiple critical infrastructure organizations—primarily in the communications, energy, transportation systems and water and wastewater systems sectors—in the U.S. and its territories, including Guam.
In February, the U.S. Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA) and Federal Bureau of Investigation (FBI) issued a warning that the group was “seeking to pre-position themselves on IT networks for disruptive or destructive cyberattacks against U.S. critical infrastructure in the event of a major crisis or conflict with the United States.” The group’s activities and escalating geopolitical tensions between China and the U.S. highlight the ever-growing connection between global events and cybersecurity.
Snowflake customer attacks. A compromise of one vendor can cripple your operations. In June 2024, attacks targeting cloud storage firm Snowflake’s customers quickly snowballed into a massive global data breach. Over 100 customer organizations were compromised via simple credential stuffing attacks and exposed, mainly because they didn’t enforce multi-factor authentication (MFA) as a secondary protection layer. Many of these companies were left grappling with the impacts of data theft and extortion.
The incident was one of several that began shifting the cybersecurity narrative toward resilience. Organizations looked hard at their data protection practices—and those of their partners—seeking ways to strengthen their digital supply chains. The “black swan” event that came next would push digital resilience to the forefront of the conversation.
The CrowdStrike “black swan” outage. In July 2024, organizations around the globe experienced the “blue screen of death” in what would soon be considered one of the largest IT outages in history. A faulty software update—not a cyberattack—was to blame, raising questions about software testing and SaaS quality standards. The outage also highlighted important lessons in digital resilience, such as preparing for your worst day, asking tough questions of your vendors and communicating openly.
The outage showed us the dark side of technological interdependence. It was a reminder that every organization will experience a black swan event at some point, whether it’s a vendor outage, a ransomware attack or something else. By embracing an “assume breach” mindset and continuously stress-testing contingency plans and processes, teams will be better prepared—mentally and operationally—to face a crisis, respond rapidly and emerge even stronger.
Global telecom espionage campaign. Multiple U.S. telecommunications companies were attacked in what U.S. FBI Director Christopher Wray has called China’s “most significant cyber-espionage campaign in history.”
The group behind the attack—known as Salt Typhoon—reportedly stole U.S. customer call records and communications from “a limited number of individuals who are primarily involved in government or political activity,” according to a joint statement released by the U.S. FBI and CISA on November 13. The attack compromised telecommunications infrastructure across the globe, impacting dozens of countries and highlighting growing risks to critical infrastructure. It has also fueled the broader debate about end-to-end encryption, building tension between protecting user privacy (through strong encryption where only the sender and recipient can access the communication) and the government’s desire to access data for law enforcement purposes (which is significantly hindered by end-to-end encryption, leading to concerns about potential criminal activity going undetected).
U.S. Treasury breach. Just weeks later, in the final days of 2024, reports emerged that Chinese state-backed attackers had breached the U.S. Treasury Department in a “major cybersecurity incident.” A letter provided to lawmakers stated that adversaries breached the department via third-party cybersecurity vendor BeyondTrust and “gained access to a remote key used by the vendor to secure a cloud-based service used to remotely provide technical support for Treasury Departmental Offices (DO) end users.” It continued, “With access to the stolen key, the threat actor was able to override the service’s security, remotely access certain Treasury DO user workstations, and access certain unclassified documents maintained by those users.”
The incident was an end-of-year bookend in a growing list of attacks on software providers—another sobering reminder that no organization is immune to attacks and a call for constant vigilance.
Next Up: A Look Ahead
So, what comes next for cybersecurity in the year ahead? Will we experience new challenges or face more of the same? In my next post, I’ll delve into five anticipated trends for the next 12 months—so watch this space.
Happy New Year!
Omer Grossman is the global chief information officer at CyberArk. You can check out more content from Omer on CyberArk’s Security Matters | CIO Connections page.





















